Decoding Microsoft & IBM History + More!
Could a single piece of software, initially designed for a niche market, lay the foundation for the personal computer revolution? The answer, surprisingly, lies in a compact operating system called MS-DOS, a crucial yet often overlooked piece of computing history.
In the early days of the personal computer, a struggle for dominance raged. Companies like IBM and Microsoft, titans of the tech world, sought to define the future of computing. It was in this environment that MS-DOS, a system with humble beginnings, would play a pivotal role. Microsoft, recognizing the potential, made a strategic move. They purchased the rights to an operating system and licensed it to IBM for use with their IBM PC language products. This decision would prove to be a turning point, setting the stage for the dominance of the PC and the proliferation of computing power.
The MS-DOS operating system, a text-based interface where users interacted with the computer by typing commands, wasn't initially conceived for mass consumption. Its creators, including the visionary software developers at Microsoft, envisioned a system that could be adapted to the specific requirements of various hardware platforms. The versatility of MS-DOS, combined with Microsoft's shrewd business decisions, would ultimately reshape the computing landscape.
- Richard Dawkins Net Worth How Rich Is He In 2024
- John Cusack Dating History Relationships More Unmarried Life
In 1982, the landscape changed significantly. Microsoft began licensing MS-DOS to other Original Equipment Manufacturers (OEMs). This was a crucial move. Companies could now tailor MS-DOS to function on their custom x86 hardware and IBM PC clones. This licensing strategy not only ensured wider adoption of the operating system but also fueled the burgeoning market for PC compatible computers. It was a masterstroke, planting the seeds of a future where PCs, running MS-DOS, would become ubiquitous in homes and offices worldwide.
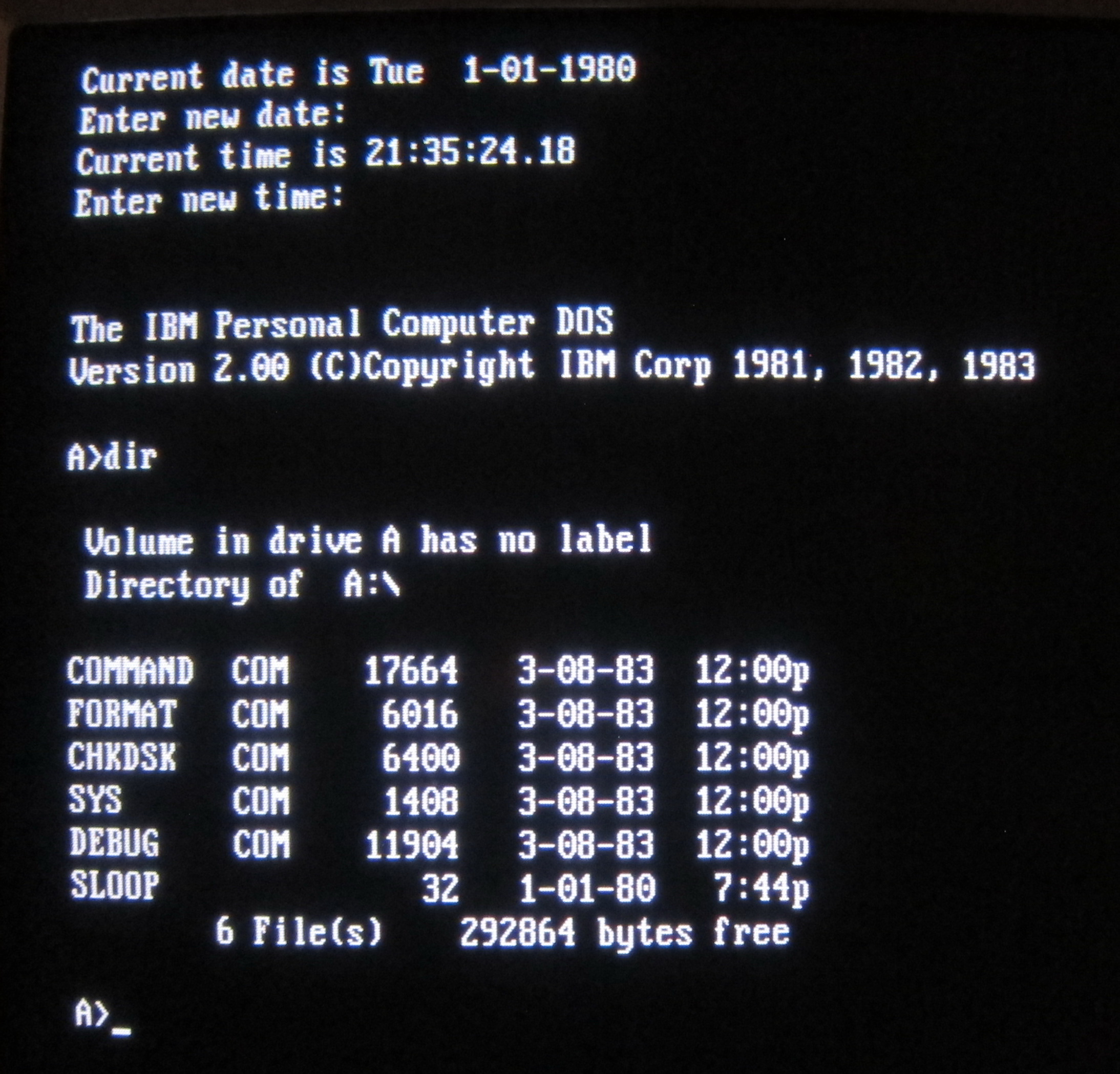
However, the MS-DOS experience was not without its complexities. At its core, MS-DOS was a relatively simple operating system. But for users accustomed to the user-friendly interfaces we take for granted today, MS-DOS presented a steep learning curve. Interacting with the system required a working knowledge of commands. For example, users needed to memorize commands such as `dir` to view a directory's contents, `copy` to duplicate files, and `del` to delete them. This command-line interface, although powerful, was a barrier for the average user. Furthermore, the hardware of the time, with limited memory and processing power, placed additional constraints on the system's capabilities.
Within the architecture of MS-DOS lies a configuration file named `msdos.sys`. This file contains a variety of settings that control how the system behaves, allowing users to customize their experience. In a sense, it was the 'control panel' for the era's operating system. There are several configurations that can be changed using this file. These settings allowed users to, for example, control the boot behavior, change the appearance of the system, and manage memory allocation. The ability to tweak these settings gave users a degree of control and personalization that was innovative at the time.
The inner workings of `msdos.sys` are noteworthy in their simplicity. Most values within this file are set to either 0 or 1. This on/off structure makes the operation of MS-DOS relatively straightforward. A value of '0' generally represents a setting that is turned off, while '1' indicates that it is activated. The binary nature of these settings exemplifies the fundamental building blocks of computing at the time.
The default user account within MS-DOS, when no other user accounts were configured, would automatically be the only one available. This simple, unadorned user experience stands in sharp contrast to the multi-user environments we have grown accustomed to today. There were no elaborate login screens, profiles or permissions, and no need for complicated password management; the system was designed for single users and minimal complexity. Although it was the default setting, the emphasis on single-user operation reflected the limited capabilities and context of the hardware and software of the time. It was the foundation, a base from which greater things would later develop.
Beyond the domain of operating systems, the term "miracle mineral solution" (MMS) surfaces, often associated with various health claims. It is important to note that, scientific and medical communities do not generally support its use and are often wary of it. Jim Humble treatment protocols, for example, highlight this caution, advising against starting treatment without carefully reviewing information. These protocols emphasize reviewing resources that offer scientific analysis and information regarding the solution's contents and uses. The user is expected to start with a foundational understanding of the material's nature before engaging in any application.
When considering the usage of MMS, the process of application often involves creating fresh doses. Protocols may specify that the user should prepare doses as needed, rather than creating a large batch in advance. This is because the solution is often described as unstable, and its efficacy depends on freshness. The dosing regimen can involve multiple doses throughout the day, designed to be taken at specified intervals. The timing of those doses, and their integration into the daily routine, is often a central focus of the dosing instructions.
In regimens involving MMS, the instructions often address the timing of meals and daily routines in relation to the dosage schedule. Recommendations may suggest finishing heavy meals by a certain time, such as 4:30 p.m., to ensure compatibility with the dosing schedule. After work hours or other daily activities, the dosing is then typically initiated. For instance, the evening doses might start around 6 p.m. and extend into the night. Proper scheduling is essential for consistent application and the perceived effectiveness of the regimen.
It is essential to approach any information encountered online with caution. While the digital world offers a wealth of information, it is also a repository for misleading or untrustworthy data. The emergence of links offering unregulated or questionable content, such as those promising exclusive content like "exclusive desi leaked viral mms videos," is a common issue. This is particularly relevant in the context of platforms where users share videos and pictures. Such platforms are often targeted at viewers with specific interests, presenting a range of contents from straightforward clips to those with potentially harmful elements.
Websites, like Masalamms.com, serve as forums where users can exchange content of various kinds. These sites host content ranging from entertainment to adult material. Some may feature specific types of content, like "desi porn," which are often created locally and cater to a particular audience. Forums and other websites often have a wide selection of content that may cater to diverse interests. The content may include videos and pictures that are freely available for users to view or download.
Similarly, platforms such as Dropmms are built for sharing content. These websites allow users to upload, watch, and download clips and images, including adult material. The websites may cater to specific interests by providing content libraries and related materials. They can serve as an avenue to share, download, and collect materials and content.
The distribution of content frequently occurs through different channels. Platforms such as "onlyfans" often serve as avenues for sharing content through subscription-based models. Here, creators can offer "exclusive collections" and "leaks." Websites can offer various contents through subscription services. These sites usually contain media of various types, depending on the preferences of the creators or service.
The use of digital platforms and content-sharing websites exposes users to a variety of materials. Some websites offer a broad selection of free content, including videos and photo collections. This content may be accessible to the public or require user registration or specific subscriptions. Users should always exercise caution and be mindful of the content they access and the potential risks.


Detail Author:
- Name : Saige Wolf
- Username : porter.lynch
- Email : nakia37@hotmail.com
- Birthdate : 1971-12-18
- Address : 709 Brandt Views Suite 713 O'Konshire, NC 48073
- Phone : +1.616.767.4112
- Company : Johnston, Rice and Dooley
- Job : Drafter
- Bio : Voluptatem odio veritatis iusto eius. Fugiat odit architecto reiciendis omnis rem. Exercitationem cumque porro modi est eveniet. Temporibus nam voluptas non et facilis.
Socials
instagram:
- url : https://instagram.com/manuela.russel
- username : manuela.russel
- bio : In sunt aut hic vero. Iste eligendi ut aut quos voluptas ut.
- followers : 3686
- following : 2241
tiktok:
- url : https://tiktok.com/@manuelarussel
- username : manuelarussel
- bio : Eius qui facilis voluptatem dicta et praesentium.
- followers : 5063
- following : 2624
twitter:
- url : https://twitter.com/russel1986
- username : russel1986
- bio : Velit aut ut modi sed sit quia sapiente libero. Quas necessitatibus qui repellat a possimus soluta sit.
- followers : 303
- following : 49